A VPN (Virtual Private Network) is a service that allows you to connect to the internet securely and privately. When you use a VPN, all of your internet traffic is routed through an encrypted tunnel to a server controlled by the VPN provider. This makes it difficult for anyone to intercept your traffic and see what you are doing online, because the data is encrypted and can only be decrypted by the VPN server. VPNs are often used to protect personal privacy, to securely access company resources, and to bypass internet censorship.
Why Is VPN Needed?
There are several reasons why you might want to use a VPN:
-
Privacy: A VPN can help protect your personal data from being accessed by third parties, such as your internet service provider (ISP) or government agencies. When you use a VPN, your internet traffic is routed through an encrypted tunnel, which makes it difficult for anyone to see what you are doing online.
-
Security: A VPN can help protect your device from being infected with malware or other cyber threats. By routing your traffic through a VPN server, you can reduce the risk of your device being exposed to malicious content.
-
Access to restricted content: In some countries, the government censors certain websites or blocks access to certain types of content. A VPN can help you bypass these restrictions and access the content you want.
-
Remote access to company resources: Many companies use VPNs to allow their employees to access company resources remotely. This can be especially useful for employees who need to access sensitive data while working from home.
-
Improved online experience: A VPN can help improve your online experience by reducing the risk of being tracked by advertisers and by allowing you to access websites that might be blocked in your region.
Types Of VPN?
There are several types of VPNs:
Remote-access VPNs: These VPNs allow you to connect to a remote network over the internet. They are often used by individuals to securely access their company’s resources when working remotely.
Site-to-site VPNs: These VPNs connect two or more networks together, allowing them to communicate as if they were on the same local network. Site-to-site VPNs are often used by businesses to connect their network to a partner’s network or to connect multiple offices to each other.
Mobile VPNs: These VPNs are designed specifically for use on mobile devices such as smartphones and tablets. They allow users to securely access the internet and company resources when using public or untrusted networks.
Free VPNs: Some VPNs offer a free service, either with limited functionality or with ads. While these can be a good option for some users, it’s important to be aware that many free VPNs have been known to sell users’ data to third parties or to engage in other questionable practices.
Paid VPNs: Many VPNs offer paid subscriptions, which typically offer more features and better security than free VPNs. If you are serious about protecting your online privacy or need access to advanced features, it’s often worth paying for a reputable VPN service.
How Does A VPN Work?
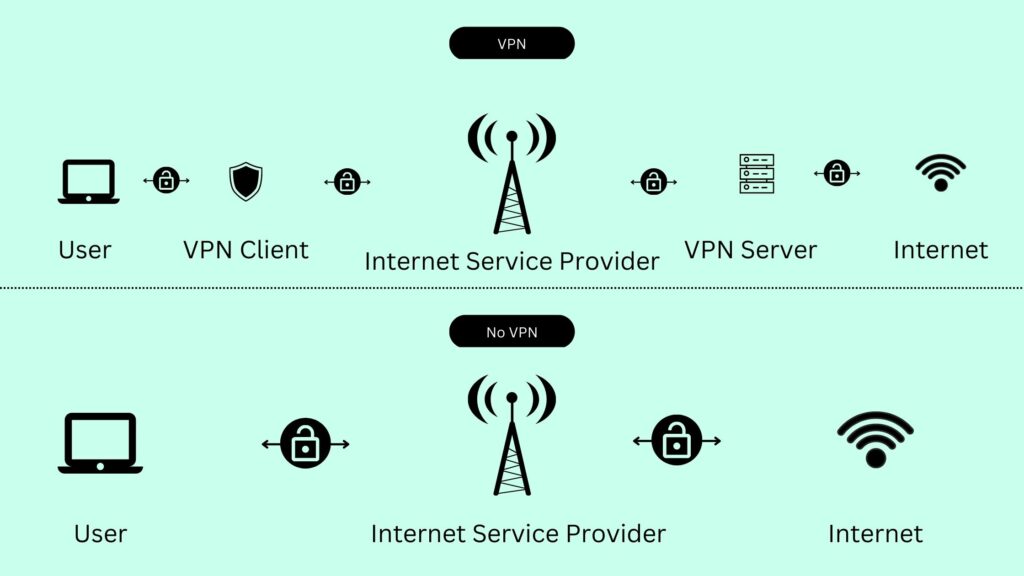
When you use a VPN, your device creates a secure connection to a VPN server. All of your internet traffic is then routed through this encrypted tunnel to the VPN server. The VPN server acts as a middleman between your device and the internet, so your online activity appears to be coming from the VPN server rather than your device.
Here’s how it works:
You connect to the VPN server by running VPN software on your device.
Your device sends a request to the VPN server to create an encrypted tunnel.
The VPN server acknowledges the request and creates an encrypted tunnel between your device and the server.
All of your internet traffic is routed through the encrypted tunnel to the VPN server.
The VPN server decrypts the traffic and sends it to its final destination on the internet.
The VPN server encrypts the response from the internet and sends it back through the encrypted tunnel to your device.
Your device decrypts the response and displays it for you to use.
By routing your traffic through an encrypted tunnel, a VPN helps to protect your data from being intercepted by third parties and keeps your online activity private.
How Do VPN Servers Operate?
VPN servers operate by routing your internet traffic through an encrypted tunnel and forwarding it to its final destination on the internet. When you use a VPN, your device creates a secure connection to a VPN server and sends a request to create an encrypted tunnel. The VPN server acknowledges the request and creates the tunnel, routing all of your internet traffic through it.
The VPN server is responsible for decrypting your traffic and forwarding it to its final destination on the internet. It also encrypts the responses from the internet and sends them back through the encrypted tunnel to your device.
In addition to routing and encrypting your traffic, VPN servers may also perform other functions, such as:
Masking your IP address: VPN servers can mask your IP address, making it difficult for websites and services to track your online activity.
Blocking ads: Some VPN servers block ads, protecting you from being tracked by advertisers and reducing the number of ads you see online.
Filtering content: VPN servers can filter content based on your location, blocking access to certain websites or online services that are not available in your region.
Improving performance: VPN servers can improve the performance of your internet connection by reducing the distance your traffic has to travel and optimizing the path it takes.
Overall, VPN servers play a crucial role in protecting your online privacy and security, and in helping you access restricted content.
What Should One Look For When Choosing A VPN?
There are several factors to consider when choosing a VPN:
Security: The security of the VPN is important because it will protect your data from being intercepted by third parties. Look for a VPN that uses strong encryption and has a good track record of security.
Privacy: Choose a VPN that has a strict no-logs policy, meaning that it does not keep any records of your online activity. This will help protect your privacy.
Speed: A slower VPN can negatively impact your internet experience. Look for a VPN that has fast speeds and minimal impact on your internet connection.
Server locations: The more server locations a VPN has, the more options you will have for accessing content from different regions.
Device compatibility: Make sure that the VPN you choose is compatible with your device.
Customer support: Look for a VPN with good customer support, in case you have any issues or questions.
Price: Compare the prices of different VPNs to find one that fits your budget. Just be aware that cheaper VPNs may not offer the same level of security and privacy as more expensive ones.
Reputation: Do some research to find out what other users have to say about the VPN you are considering. Look for reviews and testimonials to get a sense of the VPN’s reputation.
VPN Encryption Protocols
Encryption protocols are used to secure the data that is transmitted between your device and a VPN server. There are several different encryption protocols that are commonly used by VPNs, including:
PPTP (Point-to-Point Tunneling Protocol): PPTP is a fast encryption protocol that is easy to set up, but it has been found to have several security vulnerabilities.
L2TP/IPSec (Layer 2 Tunneling Protocol/Internet Protocol Security): L2TP/IPSec is a combination of two protocols that provide stronger security than PPTP, but it can be slower.
SSTP (Secure Socket Tunneling Protocol): SSTP is a Microsoft protocol that is more secure than PPTP and L2TP/IPSec, but it is only available on Windows devices.
IKEv2 (Internet Key Exchange version 2): IKEv2 is a fast and secure protocol that is good for use on mobile devices.
OpenVPN: OpenVPN is an open-source protocol that is widely regarded as the most secure and flexible option. It is available on a wide range of platforms and can be configured to use a variety of encryption algorithms.
When choosing a VPN, it’s important to consider the encryption protocol that is being used. Some protocols are more secure than others, so it’s generally a good idea to choose a VPN that uses a strong protocol such as OpenVPN.
